
 technology
technology 
New studies by NCC Group and Barracuda Networks show threat actors are increasing ransomware exploits, with consumer goods and services receiving the brunt of attacks and a large percentage of victims being hit multiple times.
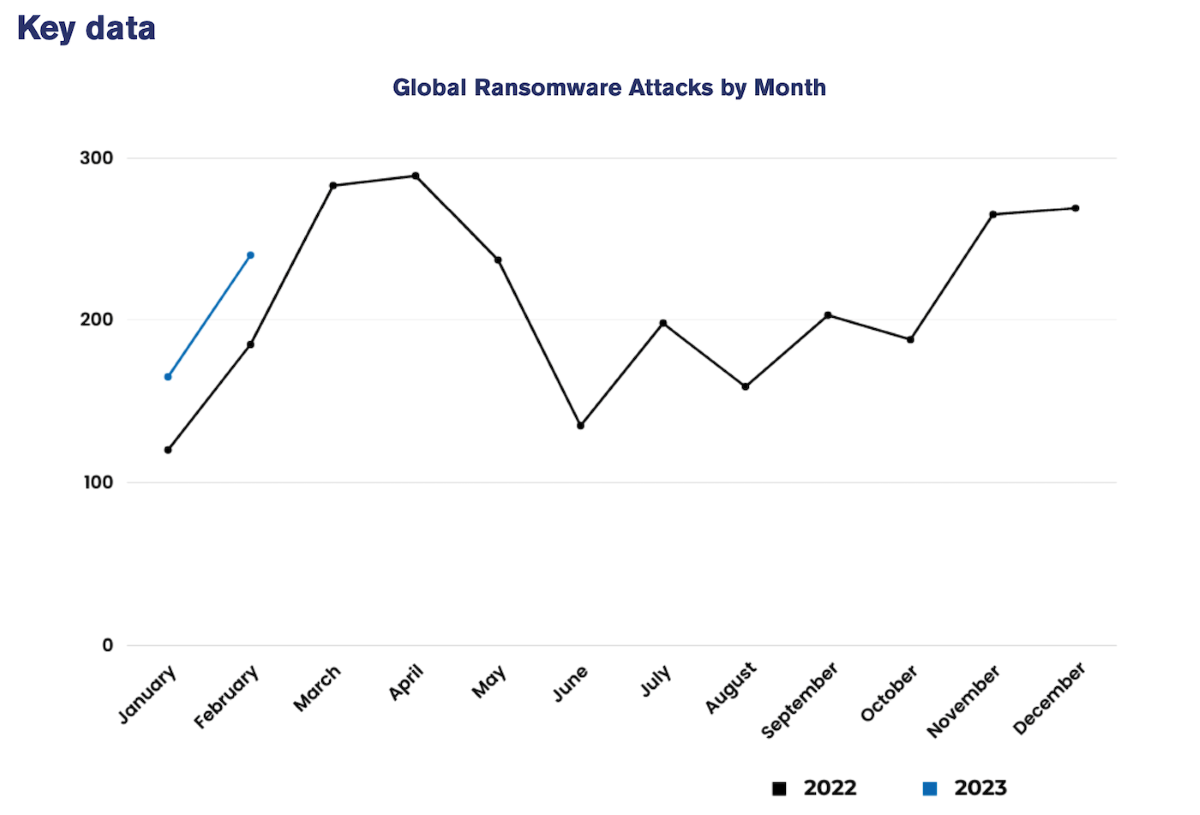
NCC Group’s Global Threat Intelligence team, in its monthly cybersecurity Threat Pulse, noted there were 240 ransomware attacks in February 2023 — a 45% increase from the record-high number of attacks in January.
In February, the volume of cybersecurity attacks was 30% above the same month both last year and in 2021, leading to January and February 2023 accounting for 405 incidents — 26% more than the period in 2021 and 38% more than in 2022, according to the report (Figure A).
Figure A
Jump to:
The NCC Group also reported that ransomware LockBit 3.0 was the leading arrowhead, with the eponymous threat group having launched 129, or 54%, of ransomware salvos last month, including an attack on the U.K.’s Royal Mail. The security group reported that LockBit’s targeting of utilities, health care and consumer staples escalated it to the top three threat actors for the first time, with 20 incidents, a 150% increase in victims in this sector since January.
SEE: CISO’s see attacks as inevitable, regardless of security posture.
Other threat actors that were busy in February included:
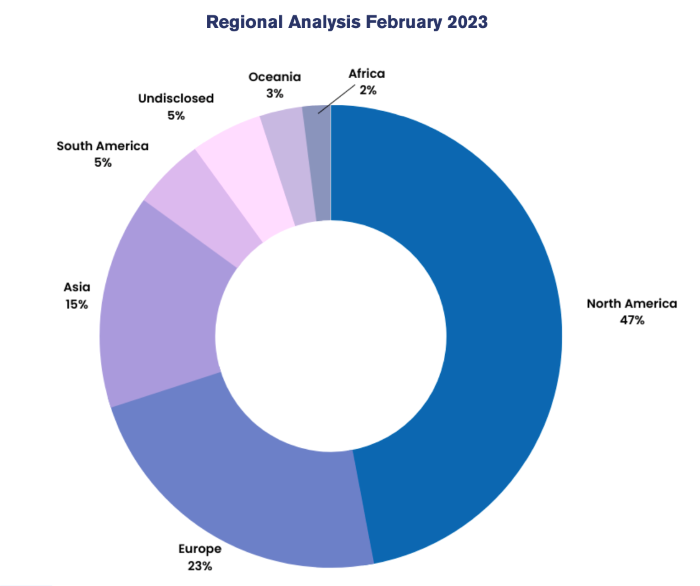
North America accounted for 47% of February ransomware activity with 113 enterprises in the crosshairs, according to NCC Group. Europe, targeted with 56 attacks, accounted for 23% of exploits, while Asia, with 35 attacks, was the target region for 15% of attacks (Figure B).
Figure B
“In February we observed a surge in ransomware activity, as expected when coming out of the typically quieter January period,” said Matt Hull, global head of threat intelligence at NCC Group. “However, the volume of ransomware attacks in January and February is the highest we have ever monitored for this period of the year.
“It is an indication of how the threat landscape is evolving, and threat actors show no signs of reducing ransomware activities.”
The top two sectors attacked during February, according to the NCC Group’s report, were industrial and consumer goods. These were followed by financials, technology and academic targets.
NCC Group’s report said industrials represented one-third, or 80 of the month’s 240 ransomware attacks, an increase of 31 attacks versus January.
Similarly Barracuda Networks’ 2023 Ransomware Insights Report, which polled leaders at companies with between 100 and 2,500 employees, saw differences in ransomware attack techniques depending on targeted business sectors. Consumer services was the most attacked sector over the past 12 months. The number of companies which received at least one ransomware attack based on their business sectors were:
Additionally, 53% of energy and utility industries reported two or more disruptive ransomware incidents, and 69% of organizations reported phishing was the initial salvo of exploits aimed at stealing credentials.
Organizations with cyberinsurance are more likely to be successfully attacked by ransomware than those without it, according to Barracuda Networks’ report. It found that 77% of organizations with cyberinsurance were hit with at least one successful ransomware attack, compared to 65% without cyberinsurance.
Seventy-three percent of all organizations in the survey — 1,300 IT professionals at companies of between 100 and 2,500 employees in Europe, Asia, the Middle East and North Africa — reported being hit with at least one disruptive ransomware attack in 2022, and 28% said they were hit twice or more (Figure C).
Figure C

The study reported that 42% of those successfully attacked three times or more paid the ransom to restore encrypted data, compared to 31% of victims of a single attack. Those attacked multiple times were also less likely to use a data backup system to help them recover.
SEE: Here are seven rules for zero trust against ransomware and phishing.
The study, detailed reasons for the relatively high percentage of repeat attacks:
Barracuda Networks’ research found that 27% of the organizations surveyed feel they are not fully prepared to deal with a ransomware attack.
“The number of organizations affected by ransomware in 2022 likely reflects the widespread availability of low cost, accessible attack tools through ransomware-as-a-service offerings,” said Fleming Shi, chief technology officer at Barracuda.
The study, noting the growth of ransomware as a service, said RaaS has made it easy for attackers without technical expertise to launch exploits.
Shi said the proportion of repeat victims suggests targets aren’t closing security gaps fast enough and that security technologies should include advanced email protection and backup as well as threat hunting and extended detection and response.
24World Media does not take any responsibility of the information you see on this page. The content this page contains is from independent third-party content provider. If you have any concerns regarding the content, please free to write us here: contact@24worldmedia.com